When I first listened to Jacob “@ioerror” Applebaum talk from the 30c3 conference in Berlin I was impressed with the number and variety of different tools the NSA was using to monitor and spy on everything. One tool I was especially interested in being an iOS user was DROPOUTJEEP, sold as allowing full access with a 100% success rate in attacking iPhones but only with physical access.
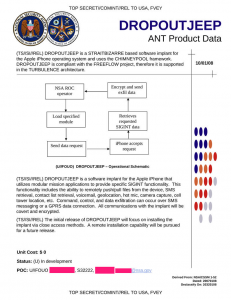 The physical access part and Apple’s flat denial got me thinking and combined with some practical knowledge about how iOS security works I am fairly sure I understand what DROPOUTJEEP is. I have broken into iOS devices to recover data and pictures for people, it’s simple for older iPhones if you have physical access.
The physical access part and Apple’s flat denial got me thinking and combined with some practical knowledge about how iOS security works I am fairly sure I understand what DROPOUTJEEP is. I have broken into iOS devices to recover data and pictures for people, it’s simple for older iPhones if you have physical access.
The earlier iPhones (before the 4S) have bootloader flaws allowing an attack on the phone before the iOS kernel boots and the kernel security kicks in. This type of attack allows the injection of a custom ramdisk image containing unsigned code. I used a ramdisk and injection tool that was assembled from an open source iOS exploit and includes an ssh server, and tools to brute force crack an iPhone PIN code using the iPhone’s own crypto hardware to accelerate the process.
The DROPOUTJEEP catalogue page is from 2008, when the iPhone 3G was the new thing, check out the timeline on Wikipedia. Most people who had an iPhone at this time remember the Limera1n jailbreak, which at it’s core is a boot loader attack. This same boot loader flaw is still unpatched even after nearly 4 years. The Limera1n attack works on the iPhone 3G onwards and there are earlier boot loader attacks too. The SHAtter boot loader attack, while never used in a jailbreak was much discussed.These types of bootloader attacks allowing the upload of custom root disks, give full hardware, disk and keybag access ie total ownage. Once your ramdisk is loaded you can just mount the internal storage and extract the data or use additional exploits to install custom malware. Full disk encryption is only a recent development, ie iPhone 3GS onwards ref: http://support.apple.com/kb/HT4175DROPOUTJEEP’s need for physical access tallies to my mind with a boot loader attack. Boot loader attacks are simple, reliable and quick so perfect for an NSA black bag job.</p>
All this is not to say that Apple can’t push remote code to an iOS device, remember Apple has the signing keys and can sign any code they like. There are reports from the early days of iMessage that Apple pushed custom remote code to a stolen iPhone to disable iMessage.
So I think that Apple are telling the truth about DROPOUTJEEP, but that is not to say they don’t cooperate in other ways when warrants or national security letters are involved.